Securing a VMware ESXi environment can be challenging, especially if you
need to meet NIST standards for data centers. NIST (National Institute of Standards and Technology)
provides guidelines and recommendations to ensure the security,
confidentiality, and integrity of data stored and processed in a data center
environment. This blog post will guide you through securing your VMware ESXi
environment to meet NIST standards for data centers.
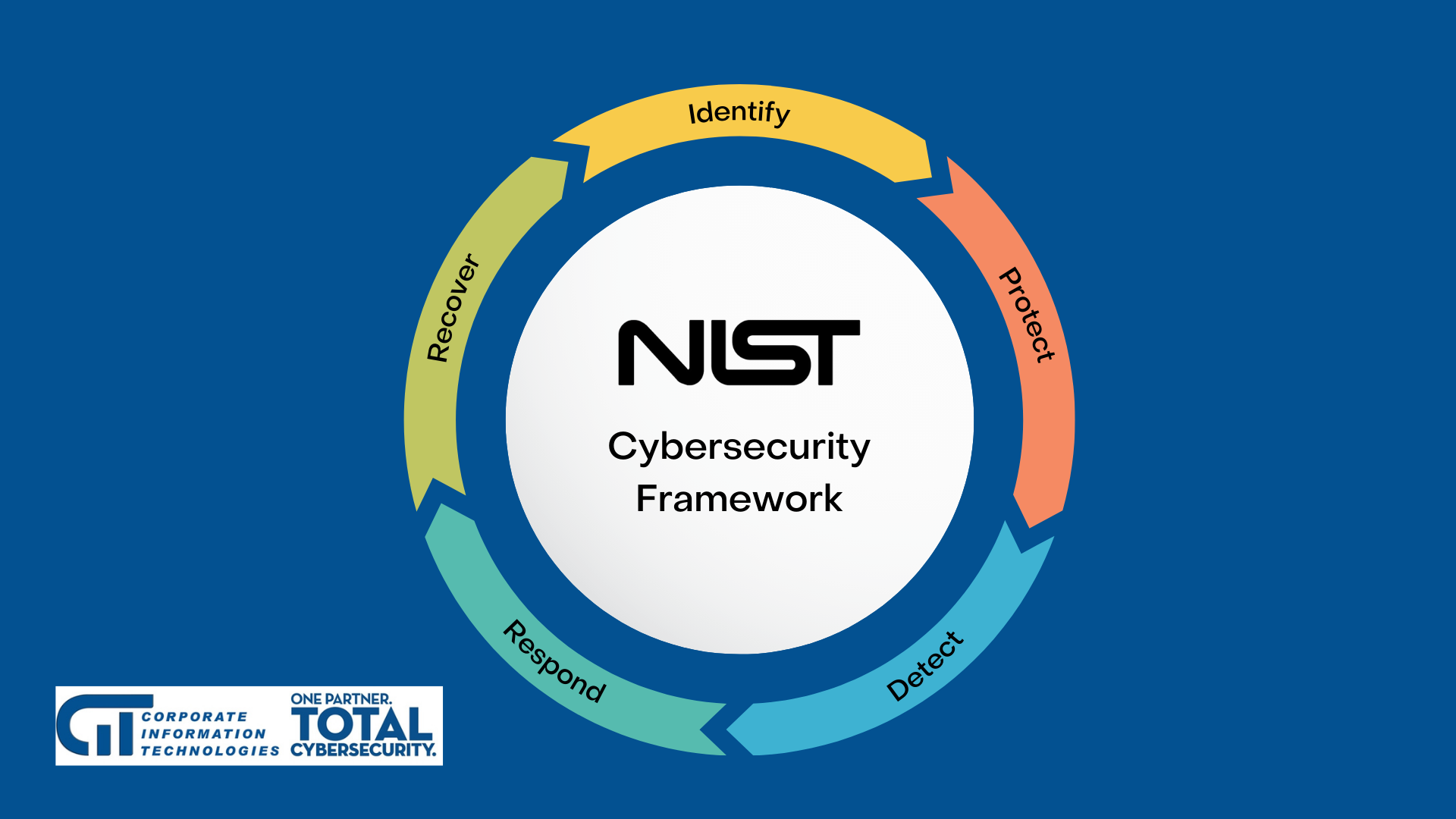
What is the NIST Standard?
The National Institute of Standards and Technology (NIST) has developed guidelines
and standards for data centers to ensure the security, confidentiality, and
integrity of data stored and processed in these environments. These standards are
known as the NIST Special Publication 800-53, and they provide a
comprehensive set of security controls that apply to all types of information
systems, including data centers.
The NIST Special Publication 800-53 is designed to help organizations implement adequate
security controls tailored to their specific needs and risk environment. The
publication provides a catalog of security controls organized into 18 families,
including access control, identification and authentication, audit and
accountability, system and communication protection, and incident response.
The NIST Special Publication 800-53 is a framework for managing security
risk and guides how to develop, implement, and assess security controls to
protect information systems. It is intended for use by federal agencies and organizations
operating information systems that support critical infrastructure, such as
financial, healthcare, and transportation systems.
The publication includes three main components: the security control
catalog, the baseline security controls, and the implementation guidance. The
security control catalog provides a comprehensive list of security controls organized
into families and categories. The baseline security controls are a subset of
the security control catalog considered essential for all information systems.
The implementation guidance provides detailed instructions on implementing and
assessing security controls.
The NIST Special Publication 800-53 is widely recognized as one of the most
comprehensive and authoritative sources of security guidance for data centers.
It is frequently used as a benchmark for evaluating organizations’ security
posture and ensuring compliance with regulatory requirements. The publication
is regularly updated to reflect changes in the threat landscape and emerging
security technologies. It is widely regarded as a living document that evolves to
meet the changing needs of the cybersecurity community.
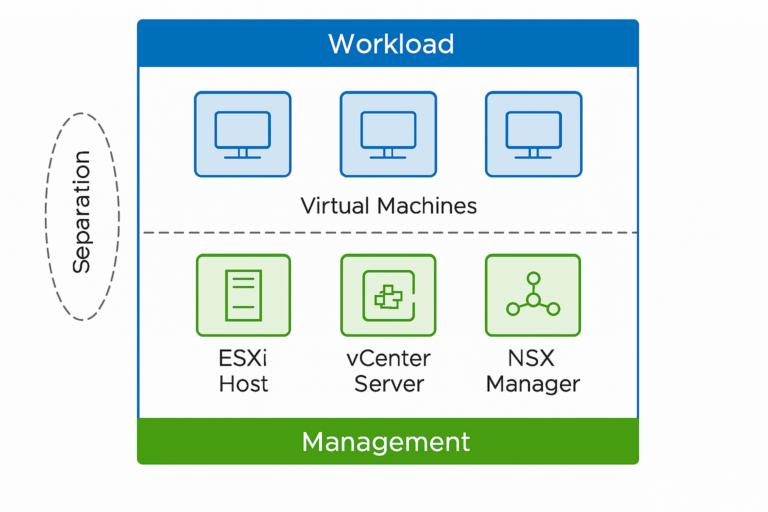
Securing ESXi
The first step in securing your VMware ESXi environment is to secure your
ESXi host. Here are some steps you can take to secure your ESXi host:
a. Enable lockdown mode: Lockdown mode restricts access to the host to
prevent unauthorized access. In lockdown mode, the only way to access the host
is through the vSphere Client. You can enable lockdown mode by navigating to
the Security Profile tab in the vSphere Client and selecting Lockdown Mode.
b. Disable unused services: By disabling unused services, you can reduce the
attack surface of your ESXi host. Some services you can disable include SSH,
Telnet, and FTP. You can disable these services by navigating to the
Configuration tab in the vSphere Client and selecting Security Profile. From
there, you can choose the services you want to disable.
c. Configure firewall rules: Firewall rules can help prevent unauthorized
access to your ESXi host. You can configure firewall rules by navigating to the
Security Profile tab in the vSphere Client and selecting Firewall. From there,
you can create rules that allow or deny traffic to and from your ESXi host.
d. Use secure passwords: Secure that all passwords used to access your ESXi
host are secure. Use strong passwords with a mix of uppercase and lowercase
letters, numbers, and special characters. Also, ensure you change your
passwords regularly and do not reuse passwords across different systems.
Secure VM
The next step is securing your virtual machines. Here are some steps you can
take to secure your virtual machines:
a. Install antivirus software on all virtual machines to protect them from
malware and other threats. Please ensure the antivirus software is up-to-date
and configured to perform regular scans.
b. Disable unnecessary services: Disable unnecessary services on your
virtual machines to reduce the attack surface. Some benefits you can disable
include Remote Desktop, Telnet, and FTP.
c. Use secure passwords: Ensure all passwords to access your virtual
machines are safe. Use strong passwords with a mix of uppercase and lowercase
letters, numbers, and special characters. Also, ensure you change your
passwords regularly and do not reuse passwords across different systems.
d. Use virtual machine encryption: Use virtual machine encryption to protect
your virtual machines from unauthorized access. You can enable virtual machine
encryption by navigating to the vSphere Client and selecting the virtual
machine you want to encrypt. From there, you can enable encryption and select
the encryption algorithm and key size.
Secure the Network
The final step in securing your VMware ESXi environment is to secure your
network. Here are some steps you can take to safeguard your network:
a. Use VLANs to isolate different types of traffic on your network. This can
help prevent attackers from gaining access to sensitive data.
b. Use firewalls to control traffic to and from your network. You can use
hardware or software firewalls to direct traffic to and from your network.
c. Use secure protocols like SSL and TLS to secure your network traffic. Secure
that all network devices, including switches and routers.
Summary
Securing a VMware ESXi environment to meet NIST Special Publication 800-53
standards requires implementing a comprehensive set of security controls. The
first step is to secure the ESXi host by enabling lockdown mode, disabling
unused services, configuring firewall rules, and using secure passwords. The
next step is to secure virtual machines by installing antivirus software,
disabling unnecessary services, using secure passwords, and enabling virtual
machine encryption. Finally, securing the network requires using VLANs to
isolate traffic, firewalls to control traffic, and secure protocols such as SSL
and TLS. The NIST Special Publication 800-53 provides a catalog of security
controls that apply to data centers and offers guidance on implementing and
assessing security controls. Adhering to these guidelines helps secure the
security, confidentiality, and integrity of data stored and processed in VMware
ESXi environments.