The principle of least privilege (PoLP) is a security concept and best practice in systems administration. It is based on the idea that a user or process should be given only the minimum privileges necessary to perform their specific tasks and nothing more.
In access control and permissions, least privilege access means that users are granted the lowest level of privileges or permissions required to carry out their authorized tasks or responsibilities. This approach aims to limit the potential damage or unauthorized access resulting from misuse, accidental actions, or intentional abuse of privileges.
By implementing least privilege access, organizations can reduce the overall attack surface and minimize the potential impact of security breaches or system failures. This concept applies to various computing environments, including operating systems, network resources, databases, applications, and cloud services.
Key principles of least privilege access include:
- Need-to-know basis: Users are granted access only to the information and resources necessary to perform their job functions.
- Principle of minimal privilege: Users are given the minimum privileges or permissions required to carry out their tasks effectively without unnecessary access to sensitive or critical resources.
- Separation of duties: Critical tasks or operations are divided among multiple users or roles to prevent individuals from having complete control or unrestricted access.
- Regular review and updates: Privileges and access rights should be regularly reviewed, updated, and revoked as needed based on changes in user roles, responsibilities, or business requirements.
By adhering to the least privilege access principle, organizations can enhance their overall security posture, limit the potential impact of security incidents, and minimize the chances of unauthorized access, data breaches, or system compromises.
How to apply to VMware
In VMware Center, we can create roles with very specific access levels. A lot of service accounts and users do not need to have admin access to the platform. Perhaps you have some admins who are only responsible for a subset of the VMs or the services.
Presumably, your VM admins do not need to make changes on the switches or be able to update the platform. Granular access gives freedom. You cannot be accountable for something you don’t have access to. Granular access makes it easier to control changes and ensure that people are trained to do the changes they perform on the system, intentionally or by accident. Your support staff may need the ability to log onto the VM, but you do not want them to be able to manage the platform.
So how do I create a role with limited access?
Log into vCenter with the user “administrator@vsphere.local ” (or what you have called the local vSphere domain).
Go to Administration in the drop-down menu at the top
Click the plus on the Roles menu
Here you have to select the function you want to give access to. As you see, it is very granular.
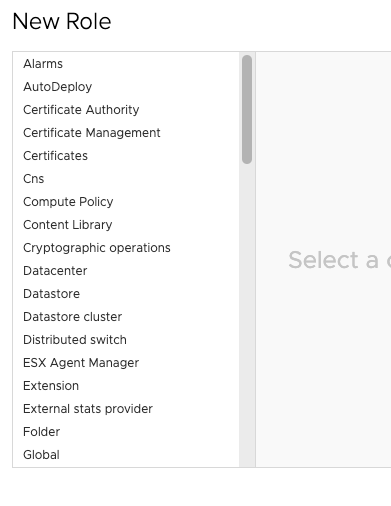
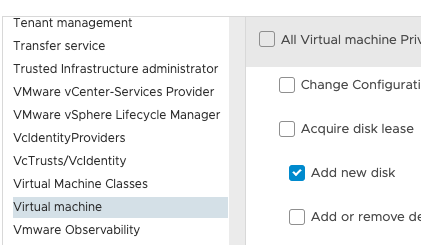
Say we want to give access to “Add new disk”, we would then go to “Virtual Machine” and select “Add new disk.” With this setting, that is all the role can do, nothing else.
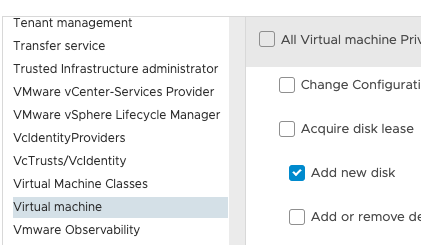
I recommend planning the level of access you want the specific roles to have. Test out the access with a user you can access before giving the level of access to anyone so you are sure you have only given the needed access. Giving out too much access will enable users to do operations you didn’t plan for them to do. I recommend checking out the configuration for roles to do common tasks. When the desired access is given, you will save that role by giving it a name.
So now I have created a role and given it a name. The next step is to assign this role to a user. Where do you want the user to have access? This might be a dumb question, but there are several levels in a Standard vCenter. It might be a global role. It might be a role you want to restrict to a vSphere cluster, a data center, a distributed switch, etc… Regardless of where you want to assign the role, it works the same way.
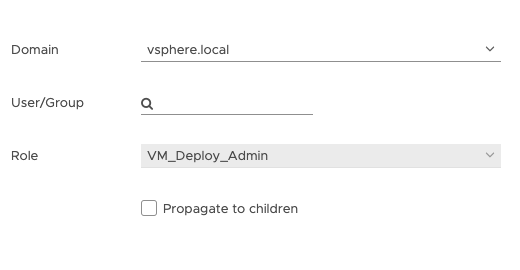
Go to the “Permissions” tab. Select the + sign. Select the Domain. This may be your connected LDAP/AD Domain. Select the user, and select the role. Check the “Propagate to children” if you want child objects to have the same access. If you do not check here, the access will only be to the object you assigned the access to.