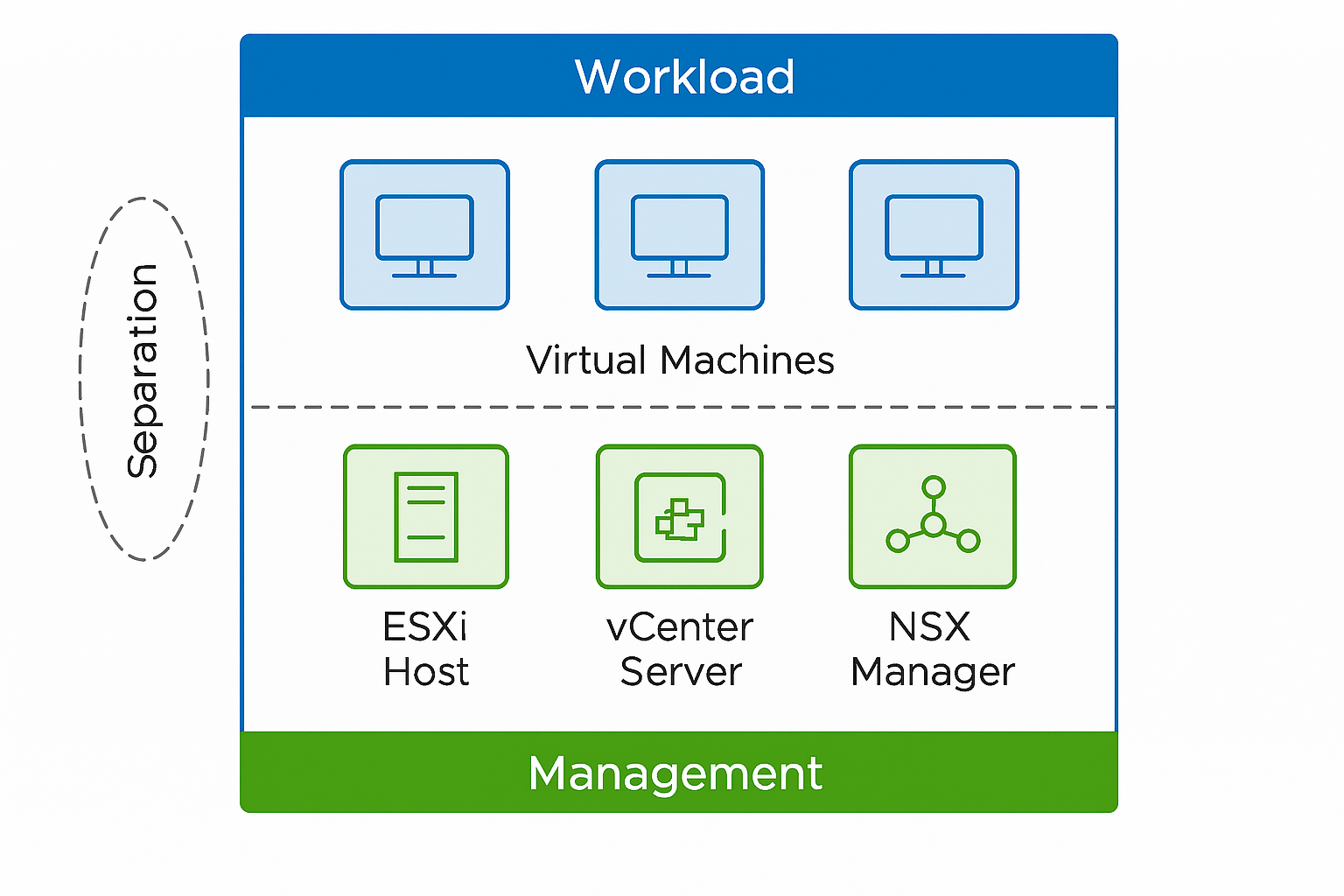
As virtualization continues to mature and hybrid cloud models become the norm, one architectural principle consistently proves itself essential for both resilience and security: the separation of workload and management.
In VMware environments—whether traditional vSphere, VMware Cloud Foundation (VCF), or hybrid deployments—isolating your management components from your general workload plane is no longer just “good practice.” It should be considered a baseline requirement for any secure and scalable environment.
In this post, I’ll break down why this separation matters, what problems it solves, and how it strengthens the overall security and operational integrity of your virtual infrastructure.
1. Reduced Attack Surface and Stronger Security Posture
Your management plane is the brain of your virtualization environment. Components like vCenter Server, ESXi host management interfaces, NSX Manager, Lifecycle Manager, and SDDC Manager control everything happening across your cluster. If attackers gain access to the management network, they gain access to everything.
Why separation helps:
- Limits exposure: Keeping management interfaces off the workload network prevents lateral movement from compromised VMs to critical infrastructure.
- Stronger ACLs & microsegmentation: A dedicated network allows strict firewall rules—often “deny all except from jump hosts.”
- Enhanced credential protection: Administrative systems, especially those using privileged credentials, stay isolated from user or application traffic.
A single misconfigured VM should never be able to “see” vCenter. Isolation ensures that.
2. Improved Stability and Predictable Performance
Workload traffic is inherently dynamic: spikes occur, new workloads arrive, and applications behave unpredictably. If management services share that same network or resource pool, you risk impacting the very components that keep your environment operational.
With separation:
- Management traffic stays stable and predictable.
- Host isolation response (like VMware HA) becomes more reliable.
- DRS and vMotion won’t flood the same network your workloads use.
- Troubleshooting becomes dramatically simpler.
When your monitoring, control, and automation tools operate on their own dedicated lanes, your entire environment becomes more resilient.
3. Clear Operational Boundaries for Security and Compliance
Many organizations face strict auditing and compliance requirements (PCI-DSS, HIPAA, SOX, NIST 800-53). A separated management plane directly supports these requirements by enabling:
- Documentable access controls
- Dedicated logging and monitoring
- Policy enforcement specific to administrative systems
- Segregation of duties (e.g., network vs. server vs. application teams)
Auditors love clean separation—it’s easy to explain, easy to measure, and easy to show evidence for.
4. Enhanced Disaster Recovery and Faster Recovery Time
When disaster strikes—ransomware, hardware failure, or simple human error—your ability to recover depends heavily on access to management components.
Keeping management isolated ensures:
- Backups and DR components are shielded from the blast radius of an outage.
- Replication paths for vCenter/NSX Manager aren’t competing with workload chatter.
- Administrative access remains available even during workload issues.
A protected management plane often means the difference between hours of downtime and days.
5. Enables Zero Trust Architecture
Zero Trust principles require:
- Minimum exposure of critical systems
- Strict identity and access controls
- Network segmentation and traffic verification
A dedicated management network is the VMware ecosystem’s natural foundation for a Zero Trust model. It creates a defensible zone around your most privileged services and provides the control points needed for:
- Conditional access
- MFA enforcement
- Network-level identity (e.g., NSX distributed firewall rules)
Without separation, Zero Trust is nearly impossible to implement effectively.
6. It’s Aligned with VMware Best Practices and Future-Proofing
VMware’s own validated designs—including VMware Cloud Foundation—mandate separation of management and workload domains.
Why? Because it allows:
- Lifecycle management at scale
- Easier upgrades and patching
- Automation frameworks (like SDDC Manager) to operate without workload interference
- Consistency across on‑prem and cloud platforms
As VMware environments evolve—especially as more customers adopt VCF—the management-workload separation becomes increasingly essential.
Final Thoughts: Make Separation the Standard, Not the Exception
If your environment still mixes management and workload traffic on the same networks, VLANs, or clusters, you’re operating with avoidable risk. The advantages of separation are clear:
✔ Better security
✔ Increased stability
✔ Easier compliance
✔ Faster recovery
✔ Alignment with Zero Trust
✔ VMware‑recommended architecture
Separating workload and management is one of those simple architectural decisions that pays dividends for years.