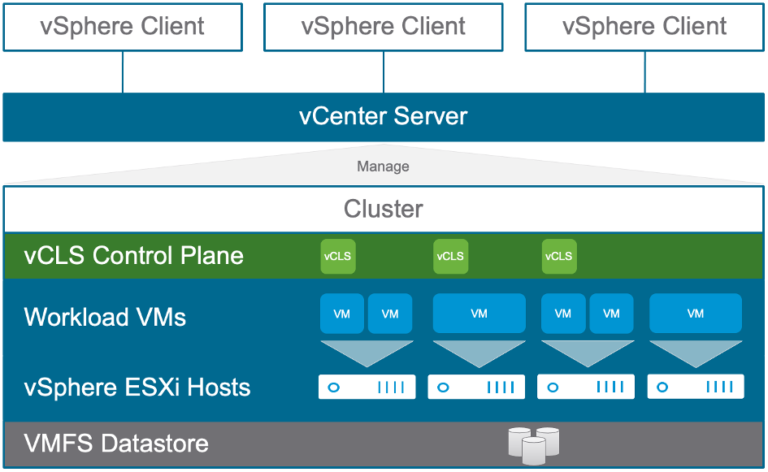
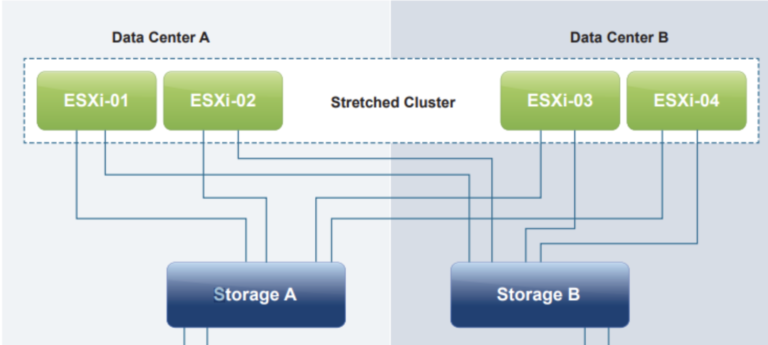
Stateless ESXi
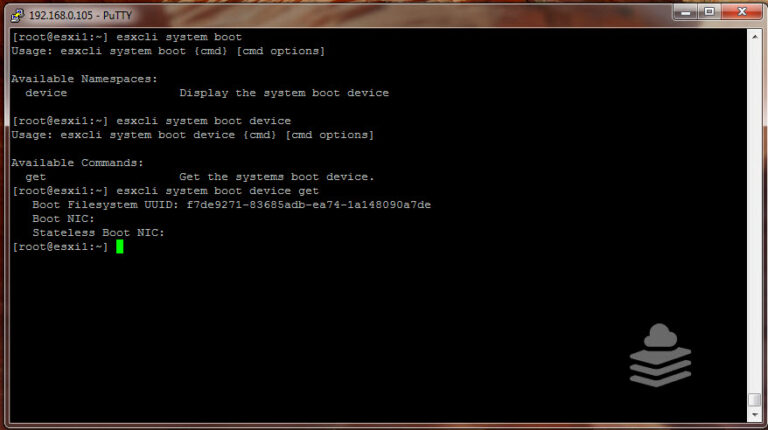
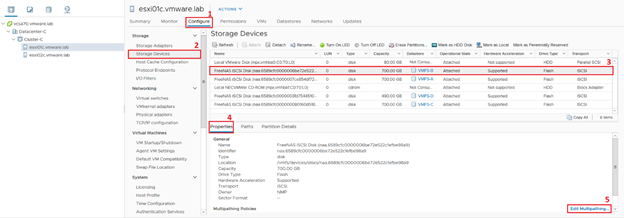
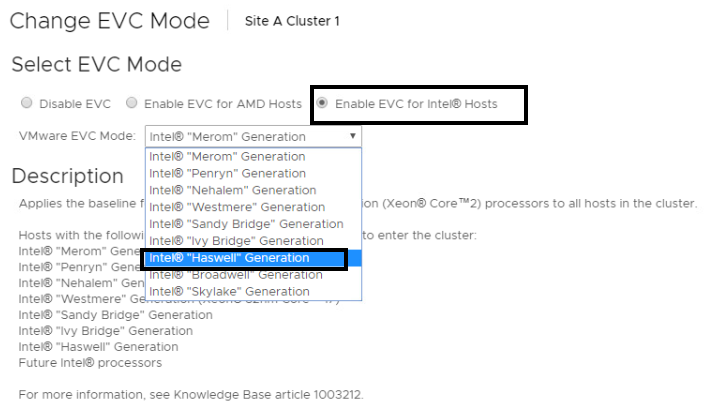
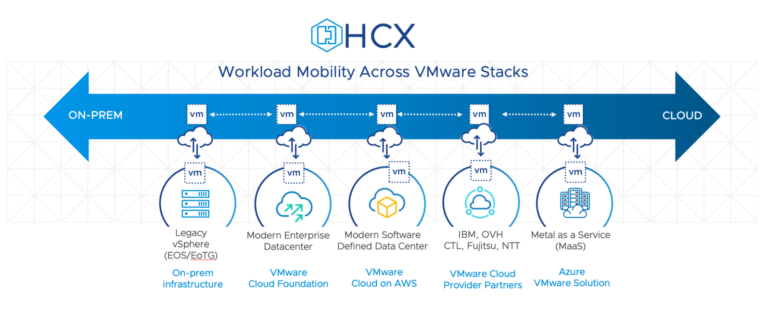
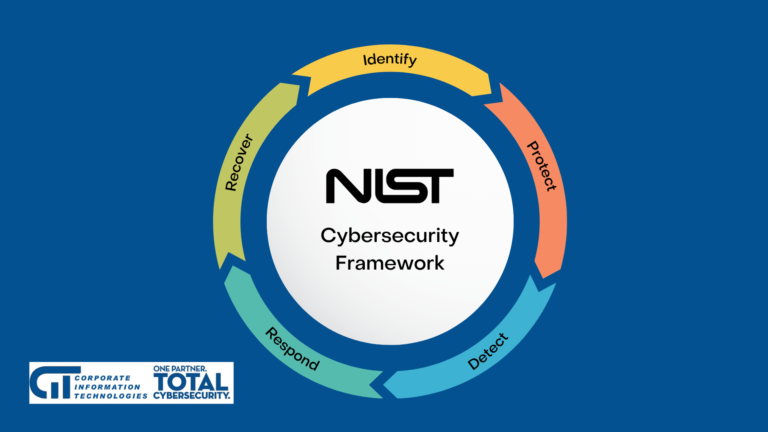
What is Stateless Stateless ESXi refers to a VMware ESXi configuration, a popular hypervisor used for virtualization. The ESXi host operates without a local disk or persistent storage in a stateless ESXi configuration. Instead, it boots over the network using…