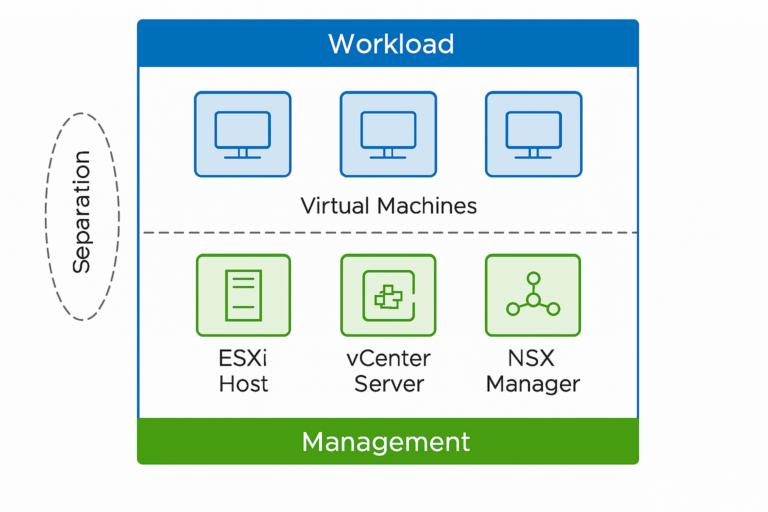
In the evolving threat landscape, vCenter Server and ESXi hosts remain high-value targets in the data center. As the foundational control and compute planes of your virtual infrastructure, securing them is essential.
Whether you’re operating in a regulated environment or simply looking to adopt best practices, this guide provides a comprehensive security baseline for hardened, resilient, and compliant vSphere deployments.
🔐 Securing vCenter Server (VCSA)
Use a Dedicated Management Network
- Segment vCenter on a management VLAN.
- Apply firewall rules to restrict access to trusted IPs or jump boxes.
- Use NSX micro-segmentation for east-west traffic control (if you have this available).
Identity Federation and MFA
- Integrate with an identity provider (Okta, ADFS, Azure AD).
- Enforce MFA for vSphere Client access.
- Avoid using
Administrator@vsphere.localfor daily use—use named accounts.
Enable and Forward Logs
- Use remote syslog to SIEM (e.g., Splunk, Aria Operations for Logs).
- Monitor for login failures, permission changes, or API abuse.
- Monitor the use of administrator@vsphere.local
Secure Services and Interfaces
- Disable unused services (Auto Deploy, Content Library if unused).
- Restrict access to VAMI (port 5480) with IP-based firewall rules.
- Rotate strong admin passwords regularly.
Patch Consistently
- Subscribe to VMware Security Advisories (VMSA).
- Use vLCM to patch vCenter and validate post-update functionality.
🛡️ Hardening ESXi Hosts
Secure Boot and Console Lockdown
- Enable UEFI Secure Boot.
- Set BIOS/UEFI and local Management passwords (idrac, ilo, etc)
- Disable ESXi Shell/SSH by default. Enable only when needed, then disable again.
Lockdown Mode
- Enable Lockdown Mode (Normal or Strict).
- Use DCUI exceptions sparingly and log usage.
Firewall and Network Segmentation
- Place ESXi Management in the management VLAN
- Use the ESXi built-in firewall (
esxcli network firewall). - Allow only required services like NTP, syslog, and management agents.
- Disable legacy services like CIM and SNMP if unused.
RBAC and Least Privilege
- Use named, non-root accounts.
- Assign roles based on duties—avoid giving Administrator roles unless needed.
- Integrate with AD or LDAP for centralized account control.
TLS and Certificates
- Replace self-signed certs with enterprise CA-signed certs.
- Disable weak TLS versions (1.0, 1.1).
- Regularly validate the certificate chain.
Logging and Monitoring
- Forward host logs to your SIEM or Aria Operations for Logs.
- Monitor for signs of brute force, host disconnects, or unsigned drivers.
Patch and Image Control
- Use vSphere Lifecycle Manager for patching and image management.
- Create and enforce a host image baseline.
- Check driver and firmware compatibility against the VMware HCL.
📐 Aligning with NIST Cybersecurity Framework (CSF)
The NIST CSF is a popular security framework used across federal, financial, and enterprise environments. Here’s how securing vCenter and ESXi maps to its five core functions:
| NIST CSF Function | VMware Action Example |
|---|---|
| Identify | Inventory VMs, vCenter components, ESXi hosts. Classify workloads and data. |
| Protect | Implement RBAC, Lockdown Mode, Secure Boot, encryption, firewall rules. |
| Detect | Forward logs to SIEM; monitor failed logins, privilege escalation, rogue devices. |
| Respond | Set up alerting and incident response via Aria Operations for Logs or SIEM integrations. |
| Recover | Use encrypted configuration and workload backups; test restores; define DR plans. |
By integrating vSphere hardening practices with the NIST CSF, organizations can align virtualization with broader compliance and audit requirements (e.g., FISMA, PCI-DSS, HIPAA).
🚀 Final Thoughts
Security is not just about ticking boxes—it’s about building resilience into your infrastructure. A hardened vSphere environment significantly reduces risk, improves operational stability, and ensures your platform is ready for the future.
As a VMware Architect, I recommend embedding these practices into your builds, maintaining them through automation and lifecycle tooling, and aligning them with your broader enterprise frameworks like NIST, ISO 27001, or CIS Benchmarks.