UEFI Secure Boot is a platform feature within the UEFI specification that ensures the system boots using only the software trusted by the hardware manufacturer. Secure Boot provides a verification mechanism in which the firmware validates a boot loader before executing it.
ESXi Server
Secure Boot is a feature in UEFI BIOS that enhances the operating system’s security, for VMware environments, ESXi, by ensuring that all boot-loaded code is digitally signed and unaltered. Additionally, it prevents attackers from bypassing your specified VIB acceptance level by using ‘–force’ at the end of the installation command.
In contrast to various operating systems, ESXi allows Secure Boot to be enabled retroactively without necessitating a full reinstallation.
To verify if Secure Boot is already enabled on your ESXi host and to assess any potential barriers to enabling it, execute the following two commands from an ESXi command line.
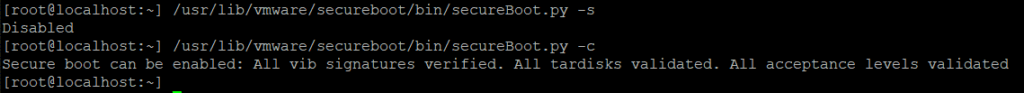
The output above indicates that Secure Boot is currently Disabled, and there are no barriers to enabling it. We can place the ESXi host in Maintenance Mode, reboot it, access the server’s BIOS setup, enable Secure Boot, and start the ESXi host again. If you’re uncertain about enabling Secure Boot, please consult your hardware server vendor for guidance.
VM
Verify that the virtual machine operating system and firmware support UEFI boot.
- EFI firmware
- Virtual hardware version 13 or later.
- Operating system that supports UEFI secure boot.
- Turn off the virtual machine. If the virtual machine is running, the check box is dimmed.
Each piece of boot software, including the bootloader, kernel, and operating system drivers, is signed in an operating system that supports UEFI secure boot. The virtual machine’s default configuration includes several code signing certificates.
The default configuration of the virtual machine includes one certificate for authenticating requests to modify the secure boot configuration, including the secure boot revocation list from inside the virtual machine. This certificate is a Microsoft KEK (Key Exchange Key) certificate.
VMware Tools version 10.1 or higher is required for virtual machines utilizing UEFI secure boot. You can update these virtual machines to a newer version of VMware Tools when it is released.
The VMware Host-Guest Filesystem is not supported in secure boot mode for Linux virtual machines. Therefore, you must remove it from VMware Tools before you activate secure boot.
Check if a VM is using UEFI
# Connect to the vCenter Server
Connect-VIServer -Server "Your_VC_Server_Name"
# Specify the name of the VM
$vmName = "Your_VM_Name"
# Get the VM object
$vm = Get-VM -Name $vmName
# Retrieve the VM's firmware setting
$firmwareType = $vm.ExtensionData.Config.Firmware
# Output the firmware type
Write-Host "The firmware type of VM '$vmName' is: $firmwareType"
# Disconnect from the vCenter Server
Disconnect-VIServer -Server "Your_VC_Server_Name" -Confirm:$false- Replace `”Your_VC_Server_Name”` with the name or IP address of your vCenter server.
- Replace `”Your_VM_Name”` with the name of the virtual machine you want to configure.
Configure a VM to use UEFI
# Connect to the vCenter Server
Connect-VIServer -Server "Your_VC_Server_Name"
# Specify the name of the VM
$vmName = "Your_VM_Name"
# Get the VM object
$vm = Get-VM -Name $vmName
# Power off the VM
Stop-VM -VM $vm -Confirm:$false
# Set the VM to use UEFI firmware
$spec = New-Object VMware.Vim.VirtualMachineConfigSpec
$spec.Firmware = "efi"
# Reconfigure the VM with the new firmware setting
$vm.ExtensionData.ReconfigVM_Task($spec)
# Power on the VM
Start-VM -VM $vm
# Disconnect from the vCenter Server
Disconnect-VIServer -Server "Your_VC_Server_Name" -Confirm:$false- Replace `”Your_VC_Server_Name”` with the name or IP address of your vCenter server.
- Replace `”Your_VM_Name”` with the name of the virtual machine you want to configure.
Now what?
If you have UEFI Secure Boot enabled, the operating system will only load packages that are signed by the vendor. Any third-party packages, including ransomware, will not be loaded during startup, making your VMware environment more secure.